IT professionals shudder at the news of big data breaches because they know that even with the latest firewall and intrusion prevention technology, it is only a matter of time before an intruder gains access to their network by way of phishing or some sort of slimy social engineering tactic. The sooner a breach is discovered, and the faster IT teams respond, the less hard-hitting the repercussions become. The key in fast response is setting intelligent security policies that sound alert when malicious actors are at work.
When Hackers Get In, Set Up Policies To Stop Them From Moving Data Out
Once in your network, intruders look for data and take it. Because you can do everything in your power and budget to prevent an intrusion, yet no security system is 100% impenetrable, the next layer of security is preventing intruders from taking or altering your data. Security device policy enforcement can be effectively leveraged to limit the impact of attacks if they circumvent initial security controls. Firewall policies have great power when preventing data exfiltration when thresholds and criteria are met or exceeded.
Put your firewall to work by making it more difficult for hackers to get in and more difficult to get data out. Doing so will make your network and the data within it as least profitable for hackers as possible. In other words, if a hacker accesses your data and starts stealing it, you want to stop them in their tracks to lessen damage.
Types of Security Policies to Write To Stop Data Breaches as They are Occurring
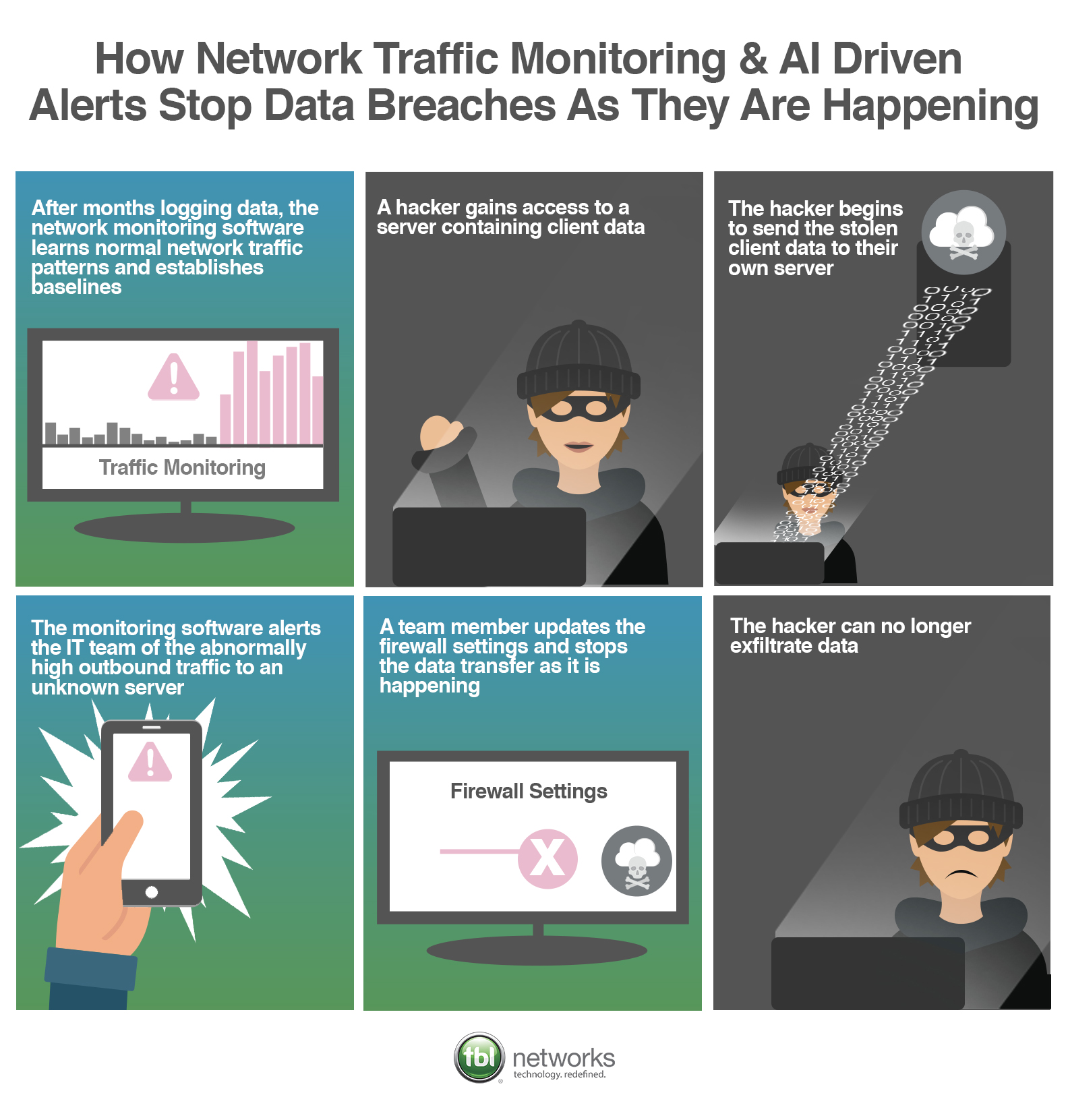
1. Volume Based: When exiting data is over a certain percentage of a well-established baseline
If data is moving at volumes above a determined percentage above established the baseline, then send an alert to the IT team to look further into.
Scenario: A hacker gains access to a server containing sensitive customer data. The hacker begins sending the data to their server. The network monitoring software detects that this is a much larger amount of data moving outside of the network than normal and an alert is issued to the IT team. The IT team updates the firewall settings and the data exfiltration is halted.
2. Location Based: When exiting data is going to an unknown location
If data is being sent to an unknown server, where business is not conducted, then send an alert to the IT team. A policy of this nature can be layered with volume as well to avoid high levels of false positive alerts.
Scenario: A hacker is sending a large amount of data to an unknown server. The monitoring system does not recognize the server and therefore sends an alert to the IT team to look into further. The team updates the firewall settings and stops that data transfer.
3. User Based: When a user's digital behavior is suddenly inconsistent with their norms
If a user is sending data at an abnormal rate at times that are not consistent with their typical working hours, then alert the IT team.
Scenario: A hacker assumes the identity of an employee and begins exfiltrating data. The monitoring system recognizes that the amount of data being transferred, coupled with the time of day is atypical. An alert is sent to the IT team to look into. They discover a hack has occurred and revoke access to the user to stop the data exfiltration.
With AI and automation you can take these policies a step further and instead of alerting, your system can revoke access without human intervention. Layering these policies on top of one another can further your security posture and prevent your company from making headlines for an attack.



