Ever increasing demands on critical networks, and their expanding sophistication places them in greater jeopardy of being compromised by bad actors. Your employees are demanding more access from a growing supply of devices and your business should support this demand. At the same time, your business needs to counter growing security threats and the specter of negative publicity surrounding data breaches. While this proliferation of BYOD practices offers freedom of choice to employees and customers (who doesn’t like this?), these policies are forcing IT departments to innovate to better secure the network. IT walks a tightrope between permitting easy access to everyone at any time, and the need to guarantee data security. Cisco’s ISE, short for Identity Services Engine, strikes that fine balance between fully supporting easy access and upholding strong network security practices.
ISE Operates on Zero Trust Principles
A zero trust policy is just what the name implies: No user is taken for granted. Neither outside, nor inside the network. In terms of Zero Trust, those seeking access are considered guilty until proven innocent.
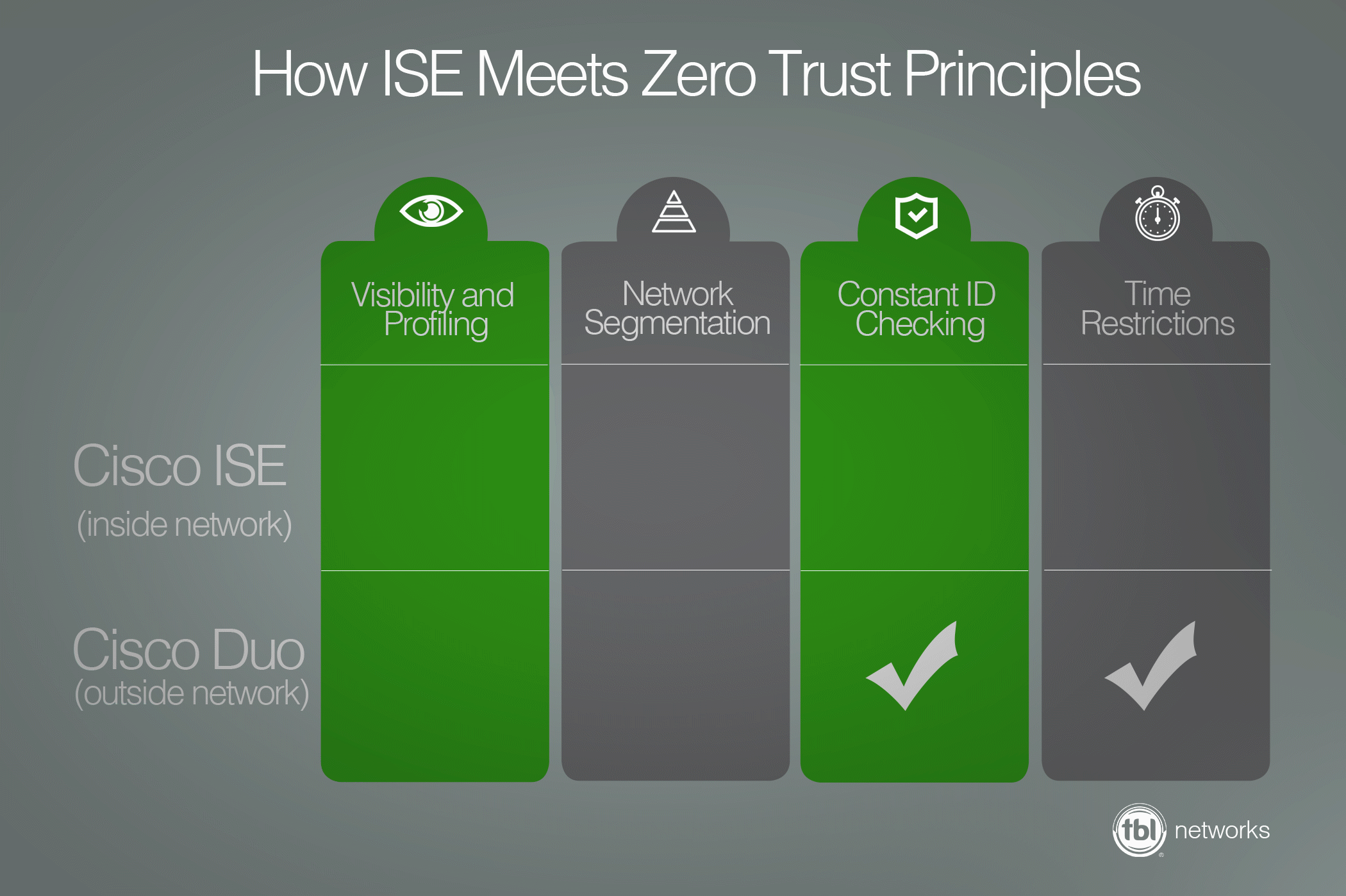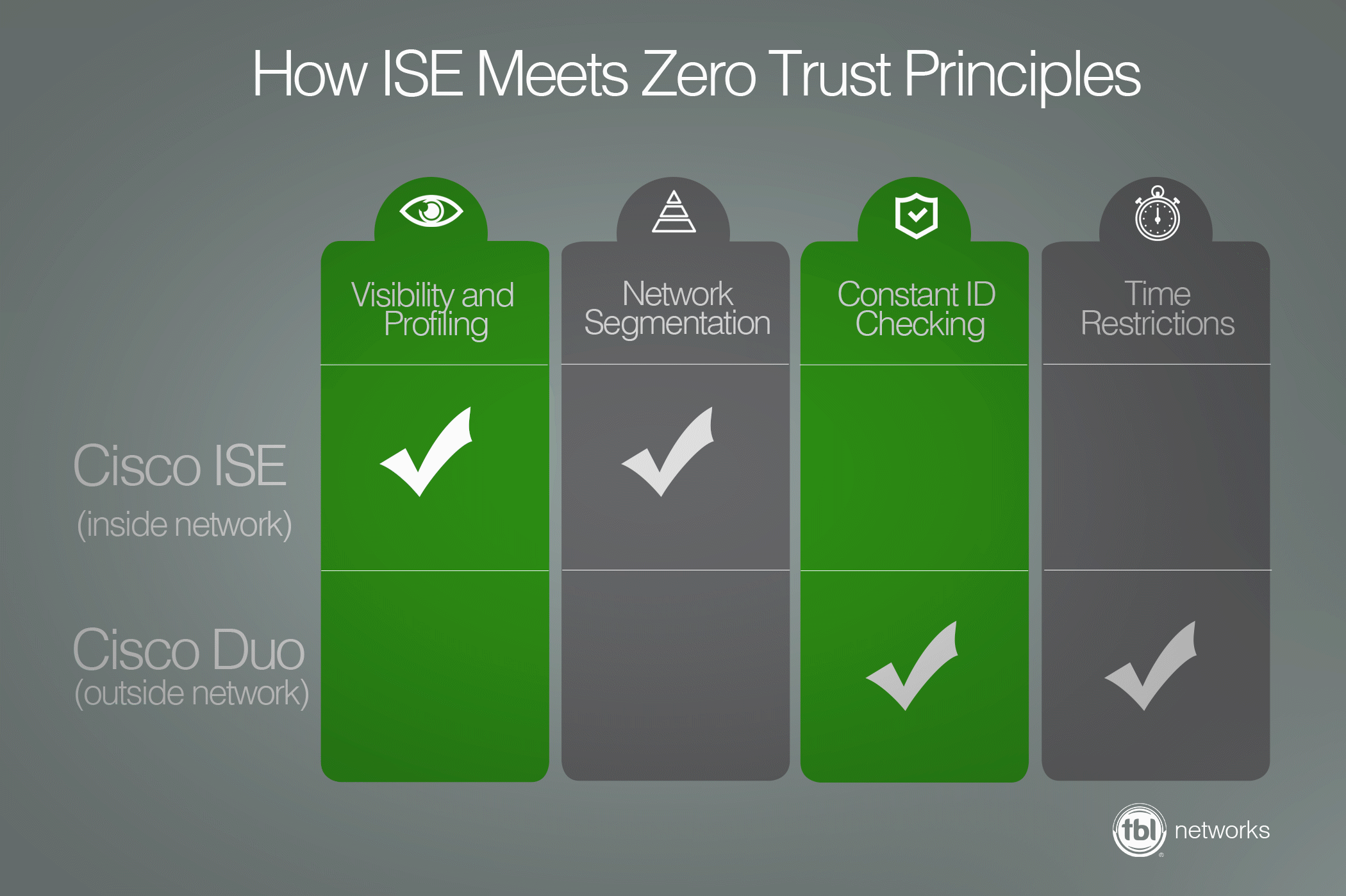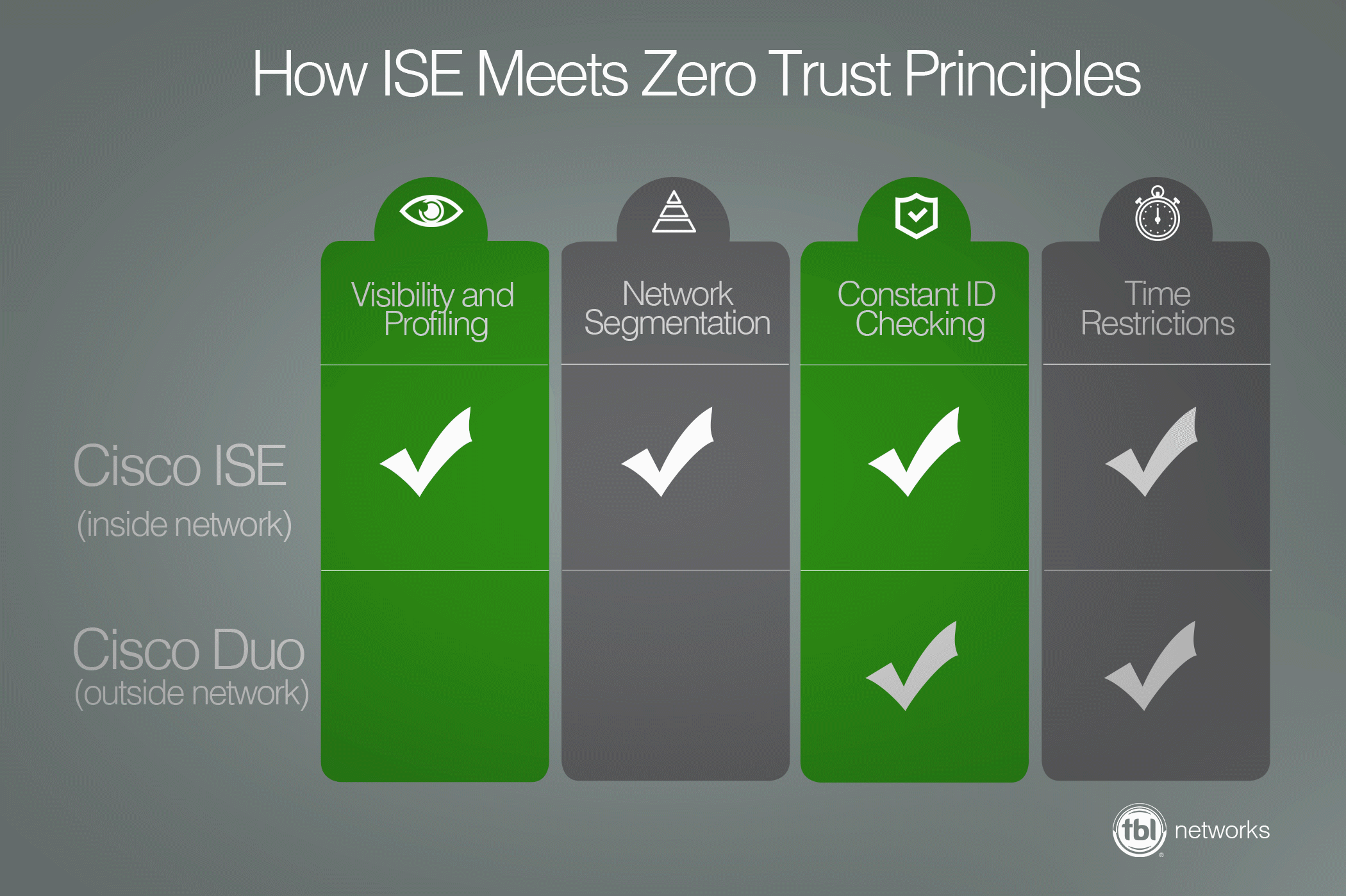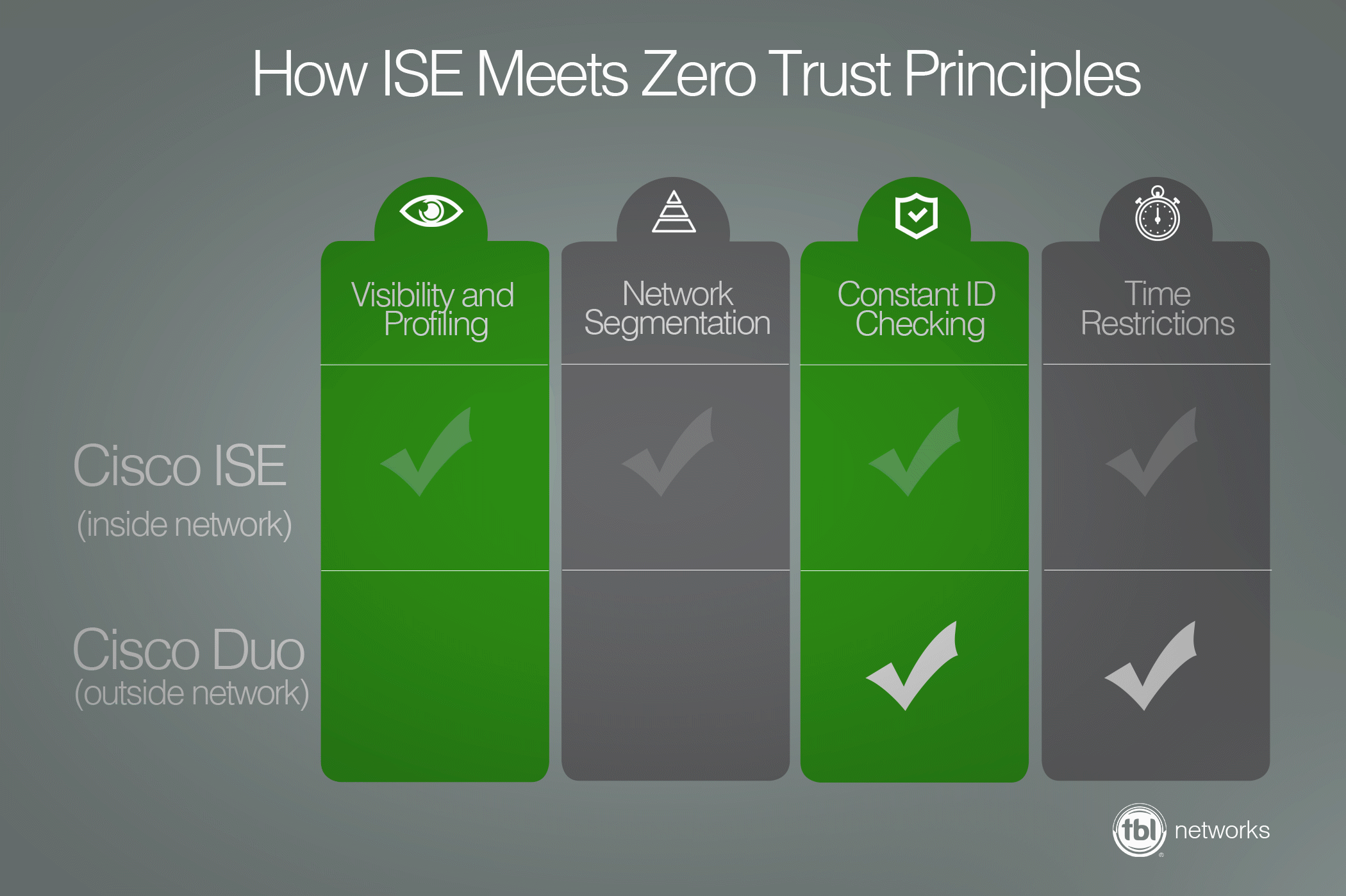
Zero trust relies on:
1. Visibility and Device Profiling
 Zero Trust Mindset: Through network usage, the behavior of specific devices and users creates predictable trends. If those trends are deviated from too far, those users and devices become suspect.
Zero Trust Mindset: Through network usage, the behavior of specific devices and users creates predictable trends. If those trends are deviated from too far, those users and devices become suspect.
Deep visibility into the users, devices, and applications traveling your network helps in winning the dynamic controls making sure only the right people with the right trusted devices get the right level of access to network services.
You must know what’s in your network before you can manage its assets.
Because it’s not humanly possible to manually profile the who, what, when, where and why of network usage, ISE has AI available for leveraging.
With ISE, profiling can be automated by device behavior, which is always more reliant than a signature alone.
To begin with device profiling, you must establish an inventory and the advent of BYOD has made this step very important.
ISE can create an inventory by:
- Discovering how many devices are accessing your network
- Showing what the devices are (from scans)
- Automatically detecting and monitoring everything on your network
Cisco has strong sensing and probing capabilities and ISE's sniffing acts on a cascade of gathered information. Many networks do not have profiling functionality because it was not required when the network was initially designed. Writing effective policies begins by knowing what is on your network.
2. Segmentation
 Zero Trust Mindset: Not all users need access to all data. Add additional protection to the most sensitive data.
Zero Trust Mindset: Not all users need access to all data. Add additional protection to the most sensitive data.
Segmentation happens once your assets are understood. Protecting your understood assets against compromised devices begins by not blindly trusting the impermeability of your perimeter. With ISE, you can build additional perimeters and boundaries around your most valuable assets within the network to stop bad actors from moving laterally.
3. Identity Checking
 Zero Trust Mindset: Just because a device has access to the network doesn’t mean the operator of that device should have access. The reverse is also true.
Zero Trust Mindset: Just because a device has access to the network doesn’t mean the operator of that device should have access. The reverse is also true.
Identity checking involves the constant monitoring of devices and user profiles. ISE upholds the boundaries you create in the network and then acts as a guard protecting those boundaries. ISE validates if the user and their associated device are worthy of receiving access across a boundary.
With ISE, sessions determine when identity checks are conducted. For example, if a device is stolen, that device must be reauthenticated. That reauthentication methods can include:
- RSA Token Servers
- SSO – single sign on
- Microsoft Azure
- SAML – security assurance markup language
- ODBC- Open Database Connectivity Identify Source
- Microsoft SQL Server
- Oracle
- Social Login
ISE:
- References specific ID checking policies and
- Supports third party identity stores. Active Directory is one of the most popular.
4. Time Restrictions
 Zero Trust Mindset: Extended amounts of inactivity could mean the device may is unattended. An unattended device can more easily be compromised or stolen by a bad actor.
Zero Trust Mindset: Extended amounts of inactivity could mean the device may is unattended. An unattended device can more easily be compromised or stolen by a bad actor.
Users who are inactive for an extended amount of time can leave your network vulnerable. For instance, if one of your users leaves their laptop unattended at a coffee shop, and a bad actor packs it up, drives away for 30 minutes, then reopens the laptop, a major security breach could ensue. To prevent this type of disaster, you can create policies for ISE to enforce based on inactivity time. This type of policy revokes access for inactive users after a predetermined amount of time has been exceeded. An inactive user will be automatically logged out by ISE once the set threshold is met.
 5. Network Security Empowerment
5. Network Security Empowerment
Zero Trust Mindset: There are many tools that work together towards a successful zero trust landscape. The orchestration of those tools is crucial.
ISE safeguards your network by leveraging its integrations with leading networking and threat defense providers.
 6. Policy Creation and Reference
6. Policy Creation and Reference
Zero Trust Mindset: There are constant fluctuations in network use and near constant attempts to enter your network. Combating these requires multiple strong defenses
ISE references and enforces policies with far greater efficiency than a person ever could. When policy thresholds are met, ISE has the power to revoke network access to any user or device. ISE doesn’t do anything that a human couldn’t do, but it scales at much better rates than a human or even a team of humans.
Cisco ISE’s Measurable Advantages
The Cisco ISE approach to network access security is comprehensive. Its advantages:
Ease of BYOD and enterprise mobility setup. You don’t have to hold back BYOD with Cisco ISE because ISE sets up right out of the box. You can use Cisco’s self-service device on-boarding and management for on-boarding both on and off premises.
Software-defined segmentation policy. Cisco’s proprietary technology enforces role-based access control at multiple layers. You can segment access dynamically without the complexity of multiple VLANs or redesigning your network.
Highly secure context-based access based on your company’s tailored policies.
ISE marshals network devices to create an all-encompassing contextual identity. Attributes include user, time, location, threat, vulnerability, and access type. This identity typically enforces a highly secure access policy that mirrors the identity’s business role. IT administrators apply controls over who, what, when, where, and how endpoints are permitted in the network.
Streamlined network visibility through a simple, flexible dashboard, and an interface that’s easy to scan.
ISE stores a detailed attribute history of all the endpoints that connect to the network. It also stores an attribute history of users (e.g., types like guest, employee, vendors, and contractors) on the network, to include endpoint application details and firewall status.
Extensive policy enforcement that defines flexible access rules for your dynamic business requirements.
This enforcement is controlled at a central location that spans enforcement across the complete network and security infrastructure. IT administrators define a policy that distinguishes guests from registered users and devices. Regardless of their location, users and endpoints are permitted based on role and policy.
Robust guest experiences offer more than one level of access to your network. For example: you can offer a cafe-type hotspot, self-service registered, or sponsored access.
Self-service device onboarding for your Bring-Your-Own-Device (BYOD) or guest policies.
Your users can manage devices based on business policies defined by IT administrators. The IT staff has all the tools available to comply with security policies. However, employees can self-serve to get their devices networked without needing help from IT.