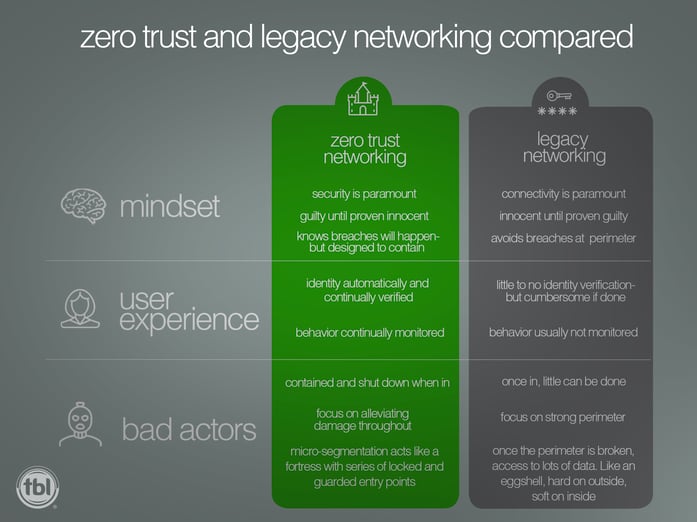
Imagine you just inherited a medieval fortress. You know, massive 30-foot stone walls. Who can climb over those walls?
It’s been neglected. There are holes in the walls in which looters climb. They have broken into long safe areas and stolen valuables.
Once upon a time, computer networks were created for connectivity. Just connectivity. Then pirates began to steal private information.
A lot like your neglected fortress.
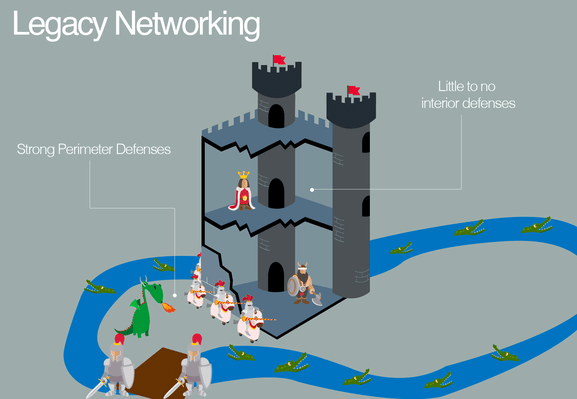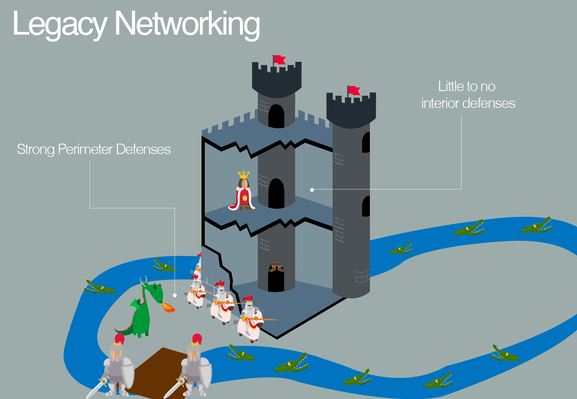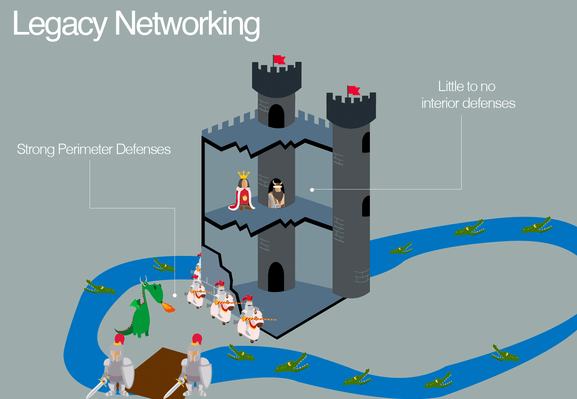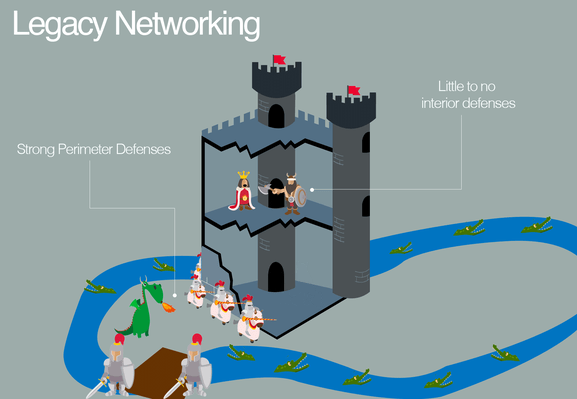
When tasked with creating a network, network architects focus primarily on accessibility and connectivity. This provides users with the seamless experience that we have all come to expect. Because of this, security in legacy networks has often been viewed as an afterthought. The best you can do is to build a strong perimeter (security) around the soft interior (network). This practice has one major flaw: once the perimeter has been breached the entire interior is compromised. The solution? Zero-Trust networking.
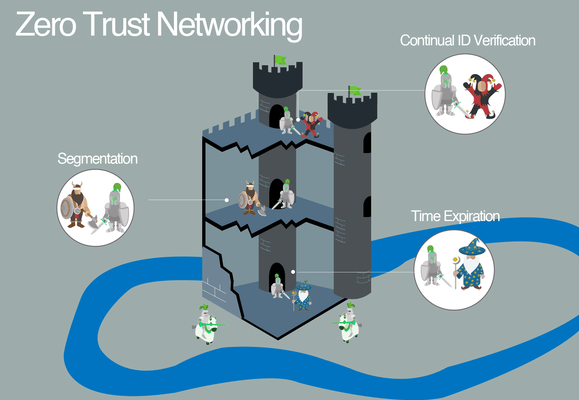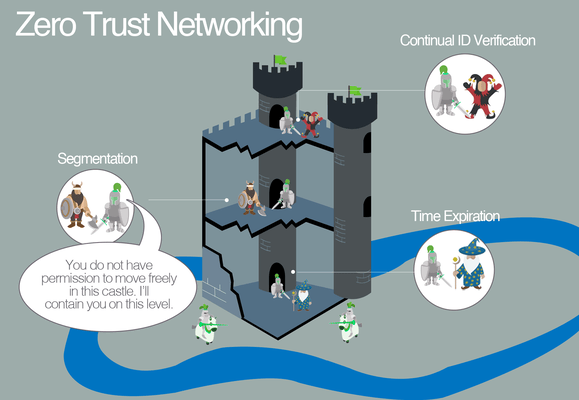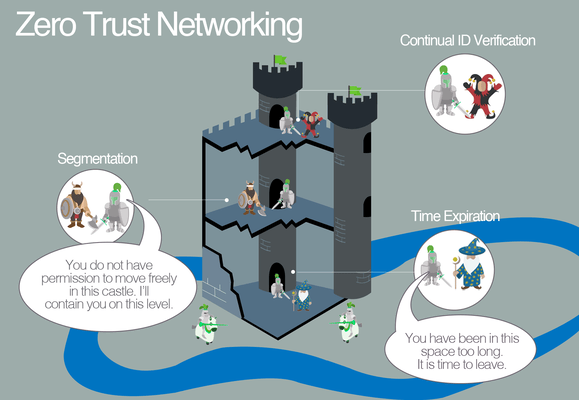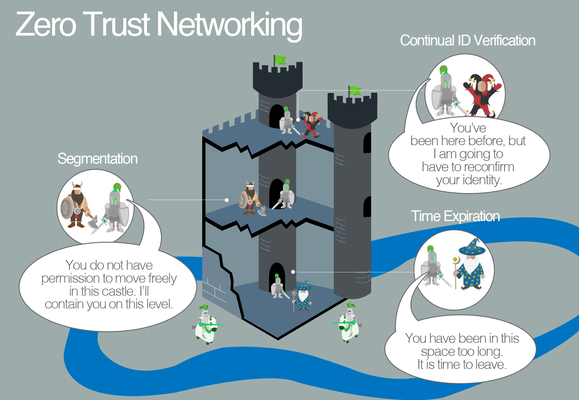
What is Zero Trust?
Back to your fortress. You immediately hire a team of security guards. The supervising guard is told to stand outside the big main door and identify every person who enters against a list you provide. If they’re not on your list, they are not able to make it past the front gate.
The remaining guards are stationed inside every room, hallway, chamber, and vault inside, to turn away uninvited guests who manage to get inside. This is what is meant by “Zero Trust”: protecting your data from intrusions anywhere in your network.
This Zero Trust concept has been championed by Google.
Back in 2006, Google suffered a major breach, and as a result, implemented Zero Trust. As in: trust no one. Do not trust those outside the company trying to access data and don't trust those on the inside (employees).
What’s the Case for Zero Trust?
The titanic conflict between networking and security teams continues. We absolutely need to rely on stable connectivity while keeping security top of mind. Networking and security seem like opposing forces.

Zero Trust is the next generation network. It provides connectivity but everything, in every network, needs to be authenticated and authorized. Nothing gains access unless verified.
Zero Trust is never “one-size-fits-all.” You can get as granular as you want with security measures.
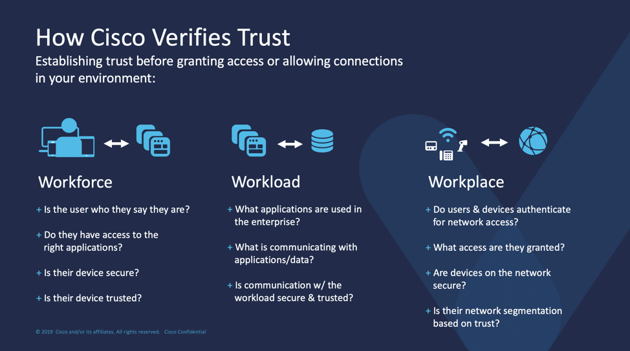
Benefits of Zero Trust
Potential for Better Future Compliance
The majority of compliance regulation was written with traditional networking in mind. For example, compliance language refers to strong perimeter defenses, a core concept in legacy networking. Compliance language refers to traditional networks, discouraging newer and better methods of networking and security.
However, regulations change. In light of highly publicized banking hacks, regulations are being updated. Compliance tends to fuse with whatever technology is available at the time of drafting. Since both Google and Cisco are championing Zero Trust, we expect compliance language will soon be updated.
One example of how regulations have not kept up with technology is the proliferation of devices.
When regulations were written, companies were only concerned about company-issued PC’s and servers. Now customers, consultants, vendors, and employees want to use their own devices to connect to your network. There are more network connected devices than ever.
More Secure Networking
Zero Trust does not have to compete with your network accessibility – it complements and enhances it. Zero Trust reduces the blind spots that have proliferated with legacy networks. It provides visibility, usually with a unified dashboard, so your security and networking teams can monitor things in real time.
It also reduces malware damages. If one machine is affected, the remainder of the network is unaffected. Your fortress stays secure because you’ve implemented security measures behind the
fortress wall.
Automation
The more manual processes you can convert safely and reliably to automation, the better your network becomes. This is also achieved at much lower price point.
TBL Networks’ Zero Trust ensures that all authentication and authorization takes place in the policy center (Cisco ISE). This means:
- Users do not need to request access. Policies are written and enforced from the start.
- Human intervention is not needed.
- If someone is promoted, and an assigned role changes, this is set up in the policy engine which updates all credentials and access.
- It scales much better as additional employees and devices are added.
Less Expensive
Zero Trust just costs less over time, because it eliminates much of the tension and conflict between networking and security teams. This typically means less overtime.
It also reduces some of the worst attacks like ransomware. Ransomware can not only require hefty payments (ransoms), but it can also damage your reputation with customers. This damage can add up to a lot more than the one-time ransom paid to hackers.
Better User Experience
Not having a network secured with Zero Trust means every employee lives in a cloud of suspicion. They need to constantly have their credentials checked for access, disrupting their work flow and concentration. No employee likes to continually enter passwords to access every bit of information within your network.
Why Is Zero Trust Not more widely adopted?
Old habits die slowly. Legacy networking has been in place for so long and it continues to have its believers, despite its proven weaknesses.
Fortunately, Zero Trust is not a budget issue. It is a mindset change, but this mindset cannot be
changed overnight.
Your fortress lasted years without direct supervision. When it became abused, you changed your mindset and hired a team of security guards. Now, you can sleep peacefully knowing that your great asset is protected from without and within.